
Use up-to-date anti-virus, anti-adware, anti-spyware programs.
Every computer needs a reputable anti-virus program. This type of utility performs virus scans, which means it attempts to inspect software on your computer before it runs, and if it finds malicious software, it either removes or disables it. Your computer should also have a good spyware scanner, which does the same thing as a virus scanner, but targets spyware and adware. Keep in mind that these programs are only effective if you keep them updated. New viruses and spyware tricks are invented every day, and your anti-virus and anti-spyware software can't protect you if it doesn't know about them.

Use a firewall.
Firewalls, which come in both hardware and software varieties, are designed to stop unauthorized people and malware from accessing your computer. Hardware firewalls are electronic devices that connect between your computer (or your network) and the Internet and block incoming communications from unauthorized sources. Using a hardware firewall allows you to protect an entire network of computers with one device. For this reason, they are often preferred by businesses and organizations.
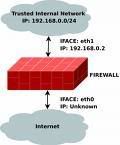
Software firewalls, on the other hand, use programs that direct the computer they are installed on to block unauthorized communications from unrecognized sources, so they're convenient for individual computer users. Most operating systems come with a built-in software firewall, but it's important to make sure it's enabled and properly configured, especially if you have a broadband connection (like DSL or cable). Broadband users need to be particularly vigilant because their computers are always connected to the Internet.

Don't open unexpected or suspicious email attachments.
Even from friends and family, unexpected attachments can cause big problems. Remember, email attachments are the most common way viruses spread. Make sure your virus scanning software is configured to scan your email and attachments. Most importantly, use common sense when downloading and opening attachments. If you don't recognize the source or are unsure what the attachment is, don't open it.

Use wireless connections cautiously.
Wireless is convenient but it isn't always secure. In fact, you should assume that any information you send or receive via a public wireless network is available for anyone to see, especially if the network is not encrypted and does not require a password. Better safe than sorry, as they say.
At home, if you're not careful, anyone with a wireless card of their own can use your wireless network and perhaps invade your computer. Take the following steps to safeguard your home's wireless network:

-Enable MAC address filtering.
Every wireless device has a unique Media Access Control (MAC) address, also known as the physical address, coded into it by the manufacturer. Many wireless routers offer a function called MAC address filtering, which allows you to restrict access to a list of approved devices. While implementing such filtering is generally a good idea, keep in mind that hackers can fake MAC addresses in order to appear to be using an approved device.
-Scramble communications over your network using the Wi-Fi Protected Access (WPA) encryption protocol.
There is also an older, out-of-date protocol available, called Wired Equivalent Privacy (WEP). Using either of these will keep neighbors or passing freeloaders off your network, but WEP won't protect you from a real cyber criminal.

Use strong passwords.
Passwords should be long preferably 10 or more characters. You can use letters, numbers and symbols and the passwords should be easy to remember and hard to guess. You also encourage to changed regularly. Avoid using logical sequences (12345 or abcdefg), repeated characters (3333333#####), adjacent letters on the keyboard (zxcvb) or passwords using only words. Using your real name or screen name is also a bad idea, as is using the same password for multiple accounts.
If your have done every thing that I told u above, you might be able to protect your personal and financial data from cyber criminals.

No comments:
Post a Comment